I’ve been on a roll lately.
A low key role. I’ve breached some of the best companies across the globe in finance/comms/defi and more.
This has attracted a ton of attention it seems. Quite often I need listeners like python http server, nc, or today an advanced TLS socket listener. Today I left it open for about 45 minutes after testing a client co and boom!, I go this :
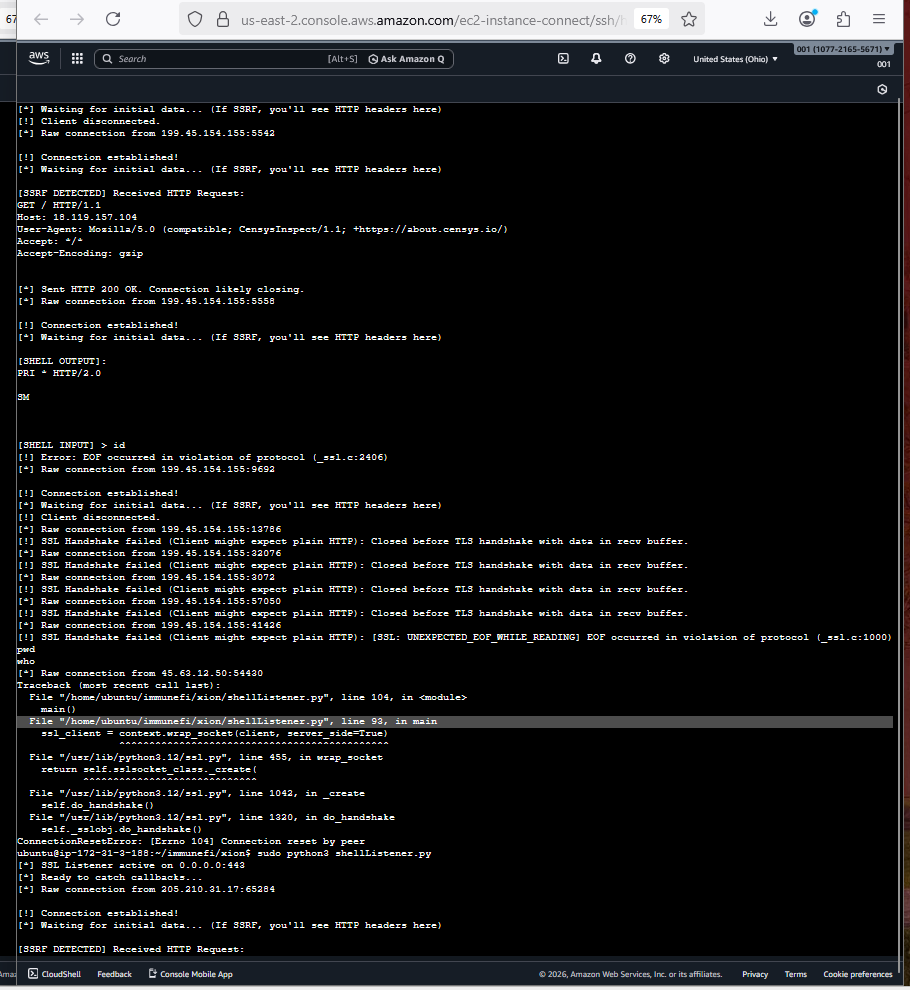
In the middle you’ll see where it says shell input. I typed Id for fun after that, becuase I was 90% sure this WASN’t the shell I was waiting for a callback on.
I see censys all the time lately, and it’s becoming obvious their tech is on an entirely different level based on what I’ve been seeing.
Whoever is running that script, is definitely waiting for their chance, thats for sure.
Later, I would get this from Palo Alto :
[*] Raw connection from 205.210.31.17:65284
[!] Connection established!
[*] Waiting for initial data… (If SSRF, you’ll see HTTP headers here)
[SSRF DETECTED] Received HTTP Request:
GET / HTTP/1.1
Host: 18.119.157.xx:443
User-Agent: Hello from Palo Alto Networks, find out more about our scans in https://docs-cortex.paloaltonetworks.com/r/1/Cortex-Xpanse/Scanning-activity
Accept-Encoding: gzip
[*] Sent HTTP 200 OK. Connection likely closing.
Leave a Reply