Introduction
In the ever-evolving landscape of cybersecurity, understanding the intricacies of an organization’s internal network and external networks is paramount. From an attacker’s perspective, gaining unauthorized access to an internal network provides a treasure trove of sensitive information and potential entry points for further exploitation. In this article, we will delve into the nuances of internal and external networks, with a focus on Network Address Translation (NAT) and the crucial role it plays in safeguarding the internal infrastructure.
Internal Network: The Fortified Citadel
An internal network is the backbone of any organization’s digital infrastructure. It comprises interconnected systems, servers, and devices that facilitate seamless communication and data exchange within the organization. The security of an internal network is of utmost importance, as it houses sensitive data, proprietary information, and critical business processes.
Anatomy of an Internal Network
Let’s take a closer look at the key components of an internal network:
- Servers: These are the backbone of the internal network, hosting applications, databases, and other services critical to daily operations.
# Sample Server Configuration
server {
listen 80;
server_name internal-server;
# ... (additional server configurations)
}- Workstations: Devices used by employees for their daily tasks, connected to the internal network to access shared resources.
# PowerShell Script for Workstation Configuration
$workstation = Get-Workstation -Name "Employee-1"
# ... (additional configurations)- Firewalls: Deployed to monitor and control incoming and outgoing network traffic based on predetermined security rules.
# iptables Configuration for Firewall
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
iptables -A INPUT -p tcp --dport 22 -j ACCEPT
iptables -A INPUT -j DROP- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): These systems play a vital role in identifying and mitigating potential threats within the internal network.
# Snort Configuration for IDS
alert tcp any any -> $HOME_NET 22 (msg:"Potential SSH Brute Force"; sid:100001;)External Network: The Perimeter Battleground
On the flip side, the external network represents the outer layer of an organization’s digital presence. It is the first line of defense against external threats, acting as a barrier to unauthorized access attempts. The external network typically interfaces with the internet and external entities, making it susceptible to a variety of attacks.
Vulnerabilities on the External Network
- Phishing Attacks: Social engineering techniques aimed at tricking individuals into revealing sensitive information or installing malicious software.
# Python Script for Phishing Attack
import smtplib
# ... (code for sending phishing emails)- Denial of Service (DoS) Attacks: Overloading a network or service to make it unavailable to users.
# DoS Attack using Hping3
hping3 --flood --rand-source -p 80 <target>- Man-in-the-Middle (MitM) Attacks: Intercepting communication between two parties without their knowledge.
# Ettercap Command for ARP Spoofing (MitM)
ettercap -T -M arp:remote /<gateway-IP>// /<target-IP>//- DNS Spoofing: Manipulating the Domain Name System (DNS) to redirect users to malicious websites.
# DNS Spoofing using Dnsmasq
dnsmasq --address=/legitimate-website.com/malicious-IPThe Role of NAT in Internal Network Security
Network Address Translation (NAT) acts as a crucial safeguard for internal networks. It involves the translation of private IP addresses used within an internal network into a single public IP address visible to external entities. This process serves multiple purposes:
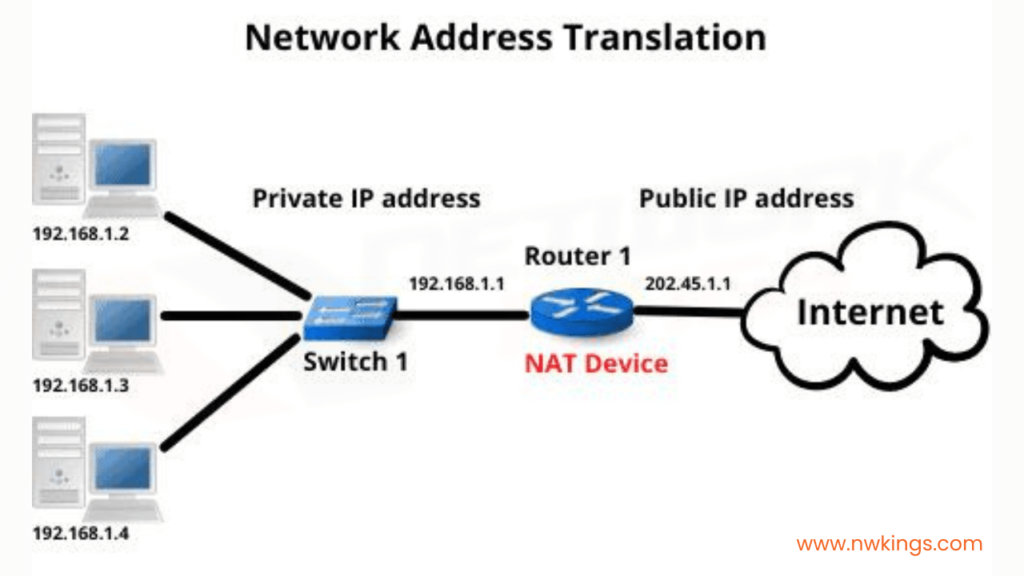
- Address Obfuscation: NAT conceals the internal network’s actual IP addresses, making it challenging for attackers to directly target internal devices.
# Sample NAT Configuration
ip nat inside source list 1 interface gigabitethernet0/0 overload
access-list 1 permit 192.168.1.0 0.0.0.255- Conservation of Public IP Addresses: Since a single public IP address is used for multiple internal devices, NAT helps conserve the limited pool of public IP addresses.
# NAT Configuration for IP Conservation
ip nat pool public-pool 203.0.113.1 203.0.113.10 netmask 255.255.255.0
ip nat inside source list 1 pool public-pool overload- Enhanced Security: By hiding internal IP addresses, NAT adds an additional layer of security, making it harder for external attackers to map the internal network’s structure.
# Enhanced NAT Security Configuration
ip nat inside source static 192.168.1.2 203.0.113.2Pentesting the Internal Network: A Case Study
To understand the vulnerabilities within an internal network, organizations often conduct penetration tests (pentests). Pentesting involves simulated cyberattacks to identify weaknesses in security controls. Let’s explore a hypothetical case study:
Case Study: XYZ Corporation
XYZ Corporation, a leading technology firm, decided to conduct a comprehensive pentest to evaluate the security posture of its internal network.
Objectives:
- Identify potential entry points for unauthorized access.
- Assess the effectiveness of firewalls and intrusion detection systems.
- Evaluate the integrity of critical servers and databases.
Methodology:
- Footprinting and Enumeration: The pentesters started by gathering information about XYZ Corporation’s internal network, including IP ranges, domain names, and employee details.
# DNS Enumeration
nslookup xyzcorp.com- Phishing Simulation: Simulated phishing emails were sent to employees to assess their susceptibility to social engineering attacks.
# Python Script for Phishing Simulation
import smtplib
# ... (code for sending phishing emails)- Exploitation and Lateral Movement: Upon gaining initial access, the pentesters sought to exploit vulnerabilities and move laterally within the internal network.
# Exploiting Vulnerabilities
exploit --target xyz-server --vulnerability outdated-software- Assessment of Security Controls: Firewalls, IDS, and IPS were tested for their ability to detect and prevent malicious activities.
# Firewall Rule Review
show running-config | include access-list- Post-Exploitation Analysis: The pentesters analyzed the extent of compromise and potential data exfiltration.
# Investigating Compromised System
grep -r "confidential" /var/log/Findings:
- Phishing Vulnerabilities: Several employees fell victim to phishing attacks, highlighting the need for improved cybersecurity awareness training.
- Firewall Misconfigurations: Inadequate firewall rules allowed for unauthorized access to certain internal resources.
- Outdated Software: Some servers were running outdated software versions with known vulnerabilities.
- Ineffective IDS/IPS: The intrusion detection and prevention systems failed to detect certain lateral movement attempts.
Recommendations:
- Strengthen employee training on identifying and reporting phishing attempts.
- Implement stricter firewall rules and conduct regular reviews of configurations.
- Enforce timely software updates and patch management.
- Enhance the effectiveness of IDS/IPS by fine-tuning rule sets and updating signatures.
Conclusion
In the dynamic landscape of cybersecurity, understanding the nuances of internal and external networks is essential for safeguarding sensitive information and critical assets. NAT plays a pivotal role in fortifying internal networks, adding an extra layer of protection against external threats.
Pentesting serves as a valuable tool for organizations to proactively identify and address vulnerabilities within their internal networks. By conducting regular assessments and implementing recommended security measures, organizations can stay one step ahead of potential attackers, ensuring the resilience and integrity of their internal infrastructure.
Leave a Reply