In the dynamic landscape of cybersecurity threats, a paradigm shift is underway with Sliver C2 emerging as one of the best internal network pentest tools, poised to supersede established counterparts like Cobalt Strike. This comprehensive Threat Analysis report, a pivotal installment in the “Purple Team Series,” is a testament to Cybereason’s commitment to unravel widely-used attack techniques. The focus here is on Sliver C2, meticulously crafted by the cybersecurity experts at Bishop Fox, and analyzed in depth by Cybereason’s GSOC and Incident Response teams.
Penetrating Insights into Sliver C2:
At its core, Sliver C2 is more than just a Command and Control (C&C) framework; it stands as one of the best internal network pentest tools in the arsenals of security professionals. Red teamers and penetration testers leverage its capabilities to remotely control compromised machines during security assessments. Simultaneously, threat actors recognize its prowess, making it a tool of choice for their nefarious activities.
Diverse Perspectives in the Purple Team Series:
The Cybereason GSOC approaches the exploration of Sliver C2 from various angles within the Purple Team Series:
- Description of the Sliver C2 framework:
Unveiling the layers of sophistication that make Sliver C2 stand out as one of the best internal network pentest tools available. - Red team aspects – getting Sliver C2 on the test bench:
Exploring how red teamers strategically incorporate Sliver C2 into their testing environments, harnessing its capabilities for optimal performance in real-life scenarios. - Blue team aspects – analyzing a past case of BumbleBee infection leading to Sliver C2 use:
Examining a practical case where the infamous BumbleBee infection paved the way for Sliver C2 deployment, emphasizing the analytical strengths of the blue team. - Purple team aspects – using blue and red knowledge, producing detections and analysis capabilities:
Merging insights from both red and blue perspectives to craft powerful detection and analysis strategies, showcasing the collaborative ethos of the Purple Team.
Strategic Alignment with MITRE ATT&CK Framework:
In an effort to enhance clarity, a comprehensive index aligns Sliver C2‘s identified features with their corresponding sections in the MITRE ATT&CK framework. This structured framework not only aids in understanding Sliver C2’s tactics and techniques but also reinforces its standing as one of the best internal network pentest tools.
Key Points Extracted by Cybereason GSOC Team:
The Cybereason GSOC team has unearthed critical aspects of Sliver C2, solidifying its reputation as one of the best internal network penetration tools:
- A burgeoning trend: Sliver C2 is gaining significant traction among Threat Actors, positioning itself as a preferred alternative to the renowned Cobalt Striker.
- Modular brilliance: The framework’s modular design, coupled with the extension package manager Armory, positions Sliver C2 as a flexible and adaptable tool for various scenarios.
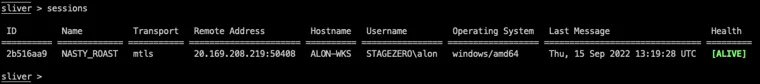
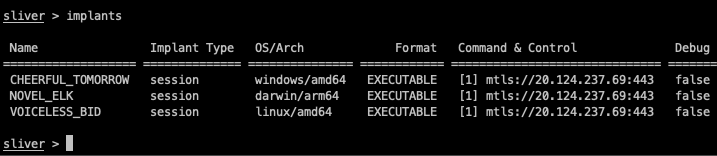
- Associations with known threat actors and malware families: Noteworthy connections, such as BumbleBee loader infections frequently leading to the deployment of Sliver C2, establish its credibility among recognized threat actors like APT29.
- Unique network and system signatures: Detection of Sliver C2 is not just a possibility; it’s a reality. The framework creates distinct signatures during execution, facilitating accurate detection and fingerprinting methodologies for the infrastructure server.
Unveiling Sliver C2’s Pinnacle Status:
What is it?
Sliver C2, positioned as one of the best internal network pentest tools, is an open-source, cross-platform adversary emulation/red team framework. Its scalability makes it an invaluable asset for organizations of all sizes engaged in security testing.
Why is it Gaining Prominence?
The meteoric rise of Sliver C2 to its status as one of the best internal network penetration tools can be attributed to several compelling factors:
- Open-source prowess: Serving as an open-source alternative to industry giants like Cobalt Strike and Metasploit, Sliver C2 stands out with unparalleled flexibility and transparency.
- Modularity enriched with Armory: The platform’s modular design, coupled with the extension package manager Armory, positions Sliver C2 as a flexible and adaptable tool for various scenarios.
- Cross-platform versatility: Operating seamlessly across OS X, Linux, and Windows environments, Sliver C2 showcases its versatility, appealing to a broad spectrum of users in the realm of security testing.
Unmatched Capabilities of Sliver C2:
The framework boasts a myriad of capabilities for adversary simulation, making it one of the best internal network pentest tools:
- Dynamic code generation
- Compile-time obfuscation
- Multiplayer mode
- Staged and stageless payloads
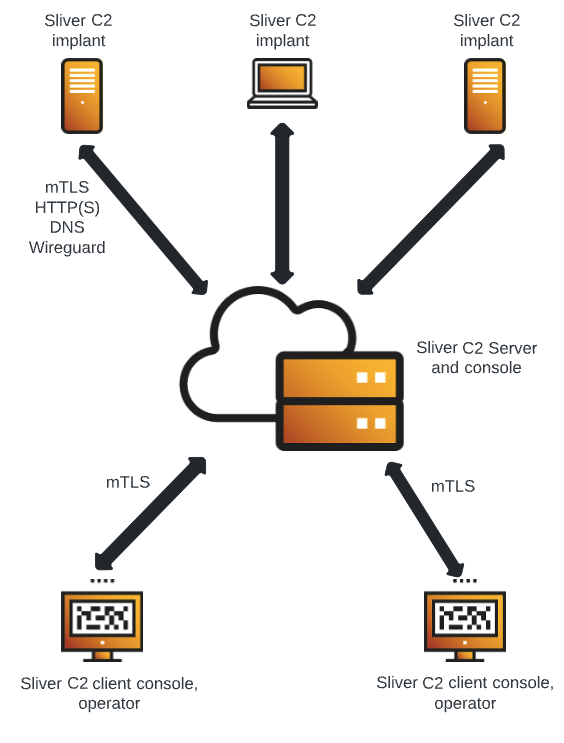
- Secure C2 over mTLS, WireGuard, HTTP(S), and DNS
- Windows process migration, process injection, user token manipulation, etc.
- Let’s Encrypt integration
- In-memory .NET assembly execution
- COFF/BOF in-memory loader
- TCP and named pipe pivots
- Armory, alias, and extension package manager
In-Depth Exploration in the Red Team Section:
Within the red team section, the report analyzes how Sliver C2, standing tall as one of the best internal network penetration tools, can be strategically leveraged in real-life attack scenarios, showcasing its unparalleled capabilities in infiltrating and navigating internal networks. This is one of the best internal network pentest tools!
Leave a Reply