Wireshark, a ubiquitous network protocol analyzer, has emerged as a cornerstone tool for network administrators, security professionals, and enthusiasts alike as 1 of the best internal network pentest tools. In this comprehensive article, we will delve into the intricacies of Wireshark, exploring its architecture, operational principles, historical debut, and the profound usefulness it offers, particularly as an internal network pentest tool.

1. Unraveling the Architecture of Wireshark:
Wireshark’s robustness lies in its modular architecture, designed to capture and analyze network traffic comprehensively. The core components of its architecture include:
- Capture Engine: At the heart of Wireshark is its capture engine, responsible for intercepting network packets. It interfaces with the network interface cards (NICs) to capture packets in real-time or from stored files.
- Dissectors: Wireshark’s dissectors decode packets into human-readable format, providing a granular view of the information exchanged over the network. Wireshark supports a myriad of protocols, each with its dedicated dissector.
- Packet Display: The packet display component visualizes the parsed information in a tabular format, allowing users to inspect packet details such as source and destination addresses, protocol types, and payload data.
- Filter Engine: Wireshark‘s filter engine enables users to focus on specific packets, reducing clutter and enhancing analysis precision. Filters can be applied based on various criteria, including source or destination IP addresses, port numbers, and protocol types.
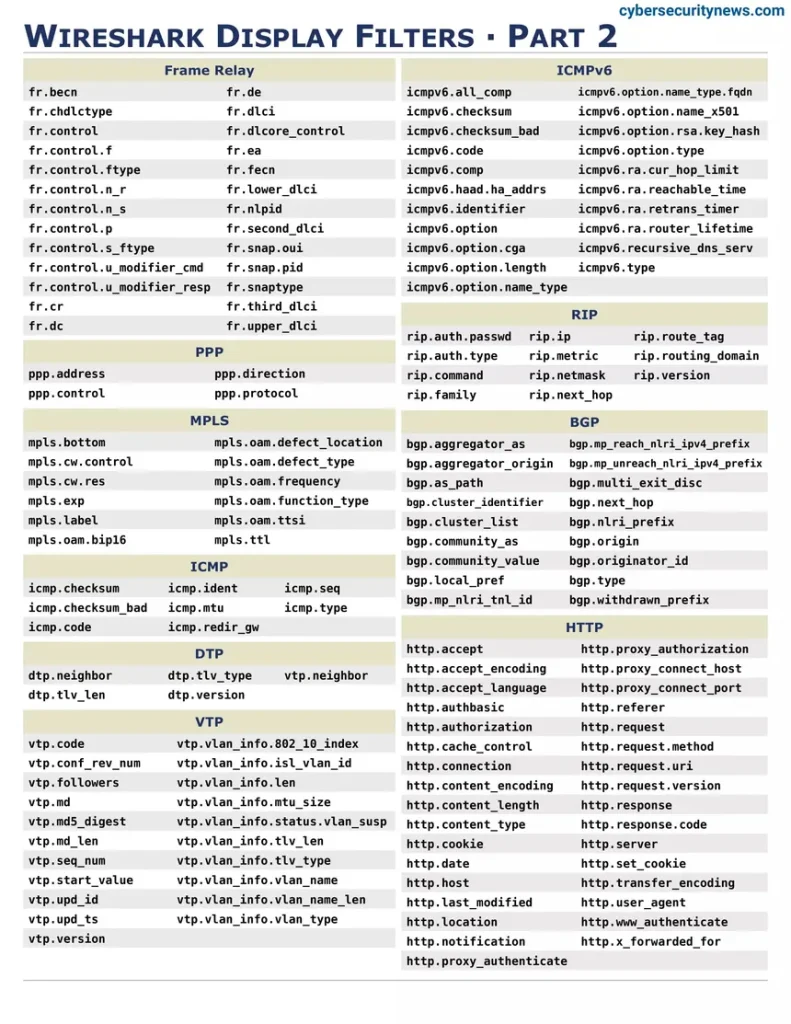
2. The Operational Mechanism of Wireshark:
Wireshark operates on the principle of passive sniffing, observing network traffic without actively participating in the communication. The process involves the following key steps:
- Packet Capture: Wireshark captures packets either in real-time or from saved files. In real-time capture, it interfaces with the NIC to capture packets as they traverse the network. When reading from saved files, Wireshark analyzes previously captured data.
- Dissection: Captured packets are dissected by protocol-specific dissectors, allowing Wireshark to interpret and present information in a human-readable format. This decoding capability extends to a wide range of protocols, from common ones like TCP and UDP to more specialized ones.
- User Interaction: The parsed packet information is displayed in the Wireshark interface, where users can interactively explore and analyze the data. The interface provides various views, including packet details, packet list, and protocol hierarchy.
- Filtering: Wireshark’s filtering capabilities enable users to narrow down their focus to specific packets of interest, facilitating efficient analysis in large datasets.
3. The Debut of Wireshark: A Glimpse into History:
Wireshark, originally named Ethereal, made its debut in 1998. Gerald Combs initiated the project with the goal of creating a network protocol analyzer that was open-source, cross-platform, and extensible. The project gained momentum, attracting contributions from a diverse community of developers.
The name change from Ethereal to Wireshark occurred in 2006 due to trademark issues. Despite the name change, the tool continued to evolve and gain popularity, becoming a staple in network troubleshooting, security analysis, and educational settings.
4. Wireshark as an Internal Network Pentest Tool:
Wireshark’s capabilities extend beyond conventional network analysis, making it an invaluable tool for internal network penetration testing. Let’s explore how Wireshark serves as a powerful asset in this context.
- Packet Inspection for Vulnerability Identification:
Wireshark aids in the identification of vulnerabilities by allowing security professionals to inspect network traffic for anomalies and potential exploits. By analyzing packets exchanged within the internal network, vulnerabilities in protocols, configurations, or insecure data transmissions can be unearthed.
- Detection of Suspicious Activity:
Internal network penetration testers utilize Wireshark to detect and analyze suspicious activity within the network. Unusual patterns, unexpected traffic sources, or unauthorized communication can be identified through careful examination of captured packets, helping assess the security posture of the internal network.
- Protocol-Level Analysis for Exploitation:
Wireshark’s protocol-level analysis capabilities prove crucial in internal network penetration testing. Security professionals can identify weak points in specific protocols, potentially leading to exploits or vulnerabilities that can be exploited for lateral movement within the internal network.
- Traffic Redirection and Manipulation:
Wireshark’s ability to capture and manipulate network traffic in real-time makes it a valuable tool for redirecting or modifying traffic during internal network pentests. This capability allows security professionals to simulate attacks and assess the effectiveness of network defenses.
- Anomaly Detection through Statistical Analysis:
Wireshark supports statistical analysis features that aid in the detection of anomalies. By analyzing network traffic patterns and statistics, security professionals can identify deviations from normal behavior, providing insights into potential security threats within the internal network.
- Incident Response and Forensics:
In the aftermath of a security incident, Wireshark plays a pivotal role in incident response and forensics. Internal network penetration testers can use Wireshark to reconstruct the sequence of events leading to a breach, helping organizations understand the scope and impact of the incident.
- User Activity Monitoring:
Wireshark facilitates the monitoring of user activities within the internal network. By capturing and analyzing packets related to user interactions with network resources, security professionals can identify unauthorized access, data exfiltration, or other suspicious behavior.
- Validation of Security Controls:
Internal network penetration testers leverage Wireshark to validate the effectiveness of security controls such as firewalls, intrusion detection/prevention systems, and network segmentation. By analyzing network traffic, they can assess whether these controls are appropriately configured and functioning as intended.
5. Wireshark’s Continued Usefulness: A Modern Perspective:
In the contemporary cybersecurity landscape, Wireshark continues to be indispensable, adapting to the evolving challenges posed by sophisticated threats. Its ongoing usefulness is reflected in several key aspects:
- Constant Protocol Support Updates:
Wireshark’s development community ensures that the tool remains up-to-date with the latest networking protocols. Regular updates and additions to protocol dissectors enable Wireshark to handle emerging technologies, ensuring its relevance in modern network environments.
- Enhanced Security Features:
Wireshark incorporates security features that contribute to its usefulness in security assessments. Secure Sockets Layer (SSL) decryption support, for instance, allows security professionals to inspect encrypted traffic, providing a comprehensive view of communication within the internal network.
- Integration with Other Security Tools:
Wireshark seamlessly integrates with other security tools and frameworks, enhancing its utility in comprehensive security assessments. Integration with intrusion detection systems, vulnerability scanners, and threat intelligence platforms amplifies Wireshark’s impact in identifying and mitigating security risks.
- Cross-Platform Compatibility:
Wireshark’s commitment to cross-platform compatibility ensures that it remains accessible across diverse operating systems. This flexibility allows security professionals to leverage Wireshark in various environments, making it a versatile tool for internal network penetration testing.
- Community Collaboration:
Wireshark’s strength lies in its vibrant and collaborative community. The continuous exchange of ideas, contributions, and shared experiences within the Wireshark community fosters innovation and ensures that the tool evolves to meet the challenges posed by the ever-changing cybersecurity landscape.
Wireshark, with its modular architecture, operational prowess, historical significance, and adaptability as an internal network pentest tool, stands as a testament to the power of open-source solutions in the cybersecurity domain. Its role in network analysis, troubleshooting, and security assessments remains unparalleled. As organizations navigate the complexities of modern networks, Wireshark’s continued relevance and impact underscore its status as an essential tool for anyone seeking to understand, secure, and optimize network communications. In the dynamic world of cybersecurity, Wireshark remains not just a tool but a beacon, illuminating the intricate landscape of network protocols and security challenges.
Title: Wireshark in Action: Harnessing the Power for Internal Network Pentesting
Introduction:
Wireshark, with its robust architecture and analytical capabilities, emerges as a formidable ally in the arsenal of tools for internal network penetration testing. In this exploration, we will delve into the practical applications of Wireshark as an internal network pentest tool. From capturing and analyzing packets to identifying vulnerabilities and simulating attacks, Wireshark’s role in the pentesting landscape is pivotal.
1. Capturing Packets: The Foundation of Network Assessment:
The cornerstone of Wireshark’s utility in internal network penetration testing lies in its ability to capture packets. This functionality provides a real-time snapshot of the network’s communication, allowing pentesters to observe, analyze, and potentially exploit vulnerabilities. The process begins with selecting the appropriate network interface for monitoring.
wireshark -i <interface>Replace <interface> with the name of the network interface you want to monitor. This simple command launches Wireshark, initiating the packet capture process.
1.1 Filtering for Relevance:
Given the vast amount of data flowing through a network, it’s essential to focus on relevant packets during an internal network pentest. Wireshark’s filtering capabilities prove invaluable in this regard. For instance, to capture only HTTP traffic, you can use the following display filter:
httpThis filter ensures that only HTTP packets are displayed, streamlining the analysis process for pentesters.
2. Identifying Vulnerabilities through Packet Analysis:
Wireshark’s prowess lies in its ability to dissect and analyze network packets at a granular level. Pentesters can use this capability to identify vulnerabilities, misconfigurations, or potential security threats within the internal network.
2.1 Detecting Unencrypted Credentials:
One common vulnerability is the transmission of unencrypted credentials over the network. By capturing packets, pentesters can inspect the payload for sensitive information. For example, capturing packets during an FTP login might reveal unencrypted usernames and passwords.
2.2 Analyzing Protocols for Weaknesses:
Wireshark’s protocol analyzers empower pentesters to scrutinize individual protocols for weaknesses. Consider the analysis of DNS traffic, where abnormal queries or responses might indicate malicious activities or misconfigurations.
dnsThis filter isolates DNS-related packets, providing insights into potential vulnerabilities or unauthorized activities.
3. Simulating Attacks with Wireshark:
Wireshark’s capabilities extend beyond passive analysis; it can be used to simulate attacks, providing a controlled environment for pentesters to assess security measures and responses within the internal network.
3.1 ARP Poisoning Attack Simulation:
Address Resolution Protocol (ARP) poisoning is a classic attack vector. Pentesters can simulate ARP poisoning using Wireshark to assess network susceptibility. This example utilizes the arpspoof tool from the dsniff suite:
arpspoof -i <interface> -t <target_ip> <gateway_ip>Replace <interface>, <target_ip>, and <gateway_ip> with the appropriate values. This attack, when executed alongside Wireshark, allows pentesters to observe the impact on network traffic and potentially assess the effectiveness of intrusion detection systems.
3.2 DNS Spoofing Experiment:
Wireshark facilitates DNS spoofing simulations, helping pentesters evaluate the network’s resilience against such attacks. Tools like dnsspoof can be used in conjunction with Wireshark for this purpose:
dnsspoof -i <interface>By analyzing DNS traffic with Wireshark during this simulated attack, pentesters can gauge the internal network’s susceptibility to DNS-based exploits.
4. Post-Exploitation Analysis:
Once an internal network is compromised, Wireshark aids pentesters in post-exploitation analysis. By capturing and examining traffic post-exploitation, they can identify lateral movement, data exfiltration, or other activities indicative of a successful attack.
4.1 Lateral Movement Detection:
After compromising a system, attackers often attempt lateral movement within the internal network. Wireshark helps pentesters identify and analyze unusual communication patterns, potentially indicating unauthorized access or lateral movement attempts.
ip.src == <compromised_system_ip> && ip.dst != <compromised_system_ip>This filter isolates traffic originating from the compromised system (<compromised_system_ip>) to identify communication with other network hosts.
4.2 Data Exfiltration Monitoring:
Wireshark proves invaluable in monitoring for data exfiltration attempts. By capturing and analyzing outbound traffic, pentesters can detect anomalies such as large file transfers or unusual data patterns that might indicate a data breach.
ip.dst == <external_server_ip> && tcp.dstport == 80This filter focuses on traffic destined for a specific external server (<external_server_ip>) on port 80, where HTTP-based data exfiltration might occur.
5. Wireshark in Forensic Analysis:
Wireshark is a potent tool for forensic analysis during internal network penetration tests. When incidents occur, Wireshark captures a detailed record of network activity, aiding in the reconstruction of events and understanding the extent of the compromise.
5.1 Investigating Security Incidents:
In the aftermath of a security incident, pentesters can use Wireshark to investigate and understand the sequence of events leading to the compromise. By examining captured packets, they can identify the initial point of entry, lateral movement, and actions taken by the attackers.
5.2 Network Forensic Analysis:
Wireshark’s ability to capture and analyze traffic over an extended period makes it a valuable tool for network forensic analysis. Pentesters can examine historical data to trace the origin and impact of security incidents within the internal network.
tcp.analysis.flagsThis filter identifies packets with TCP flag-related issues, potentially indicating abnormal network behavior.
6. Integration with Other Pentest Tools:
Wireshark’s compatibility with other pentest tools enhances its effectiveness in internal network assessments. By integrating Wireshark with tools like Nmap, Metasploit, and Snort, pentesters can create a comprehensive testing environment.
6.1 Nmap Integration for Target Discovery:
Wireshark and Nmap can be seamlessly integrated to enhance target discovery during internal network pentests. Nmap scans can provide initial insights, and Wireshark can then be used to capture and analyze the resulting network traffic.
nmap -sn <target_range> && wiresharkThis command combines a ping scan (-sn) with Nmap and launches Wireshark to capture traffic during the discovery phase.
6.2 Metasploit Integration for Exploitation:
Wireshark and Metasploit integration streamlines the exploitation phase. By capturing packets during Metasploit exploits, pentesters gain insights into the success or failure of their attacks, aiding in the refinement of strategies.
msfconsole -q -x "use exploit/<exploit_module>; set RHOSTS <target_ip>; run; exit" && wiresharkThis command automates Metasploit exploits and launches Wireshark to capture traffic during the exploitation process.
7. Wireshark’s Ongoing Relevance in the Cybersecurity Landscape:
Wireshark’s utility as an
internal network pentest tool remains unparalleled in the dynamic cybersecurity landscape. Its continued relevance is evident in several key aspects:
7.1 Continuous Protocol Support Updates:
Wireshark’s development community ensures that the tool remains updated with the latest networking protocols. Regular updates to protocol dissectors enable Wireshark to handle emerging technologies, ensuring its applicability in modern network environments.
7.2 Enhanced Security Features:
Wireshark incorporates security features that contribute to its usefulness in security assessments. Features like SSL decryption support allow pentesters to inspect encrypted traffic, providing a comprehensive view of communication within the internal network.
7.3 Cross-Platform Compatibility:
Wireshark’s commitment to cross-platform compatibility ensures accessibility across diverse operating systems. This flexibility allows security professionals to leverage Wireshark in various environments, making it a versatile tool for internal network penetration testing.
7.4 Community Collaboration:
Wireshark’s strength lies in its vibrant and collaborative community. The continuous exchange of ideas, contributions, and shared experiences fosters innovation and ensures that the tool evolves to meet the challenges posed by the ever-changing cybersecurity landscape.
Conclusion:
Wireshark’s multifaceted role as 1 of the best internal network pentest tools makes it an indispensable asset for security professionals as one of the best internal network pentest tools. From capturing packets and identifying vulnerabilities to simulating attacks and aiding in post-exploitation analysis, Wireshark stands as a linchpin in the penetration tester’s toolkit. Its ongoing relevance, continuous development, and integration capabilities underscore its significance in navigating the complexities of internal network security. As organizations strive to fortify their networks against evolving threats, Wireshark remains not just a tool but a beacon, illuminating the path to a more secure and resilient digital landscape.
Leave a Reply