In the intricate tapestry of wireless network pentesting, the Hak5 WiFi Pineapple emerges not just as a tool but as a virtuoso, seamlessly intertwining with the delicate nuances of the 802.11 protocol. This comprehensive exploration aims to unravel the layers of the WiFi Pineapple’s dance with 802.11, providing an in-depth look into its strategic traffic interception capabilities. As we delve deeper into this intricate symphony, we’ll spotlight how the device elegantly navigates the wireless networking standard, emphasizing its pivotal role in shaping the art of wireless network pentesting scenarios.

Decoding the 802.11 Protocol: A Prelude to Pentesting Mastery
At the heart of the WiFi Pineapple’s prowess lies the 802.11 protocol, the melodic language of Wi-Fi devices as they converse over the airwaves. This wireless networking standard dictates the orchestration of data frames, channels, and SSIDs, laying the foundation for the WiFi Pineapple’s strategic maneuvers in the realm of wireless network pentesting.
Essential Components of the 802.11 Protocol:
- Frames: The protocol encapsulates data within frames, ranging from management frames orchestrating connections to control frames managing network access and data frames carrying the payload.
- Channels: Operating within specific channels in the radio frequency spectrum, Wi-Fi networks create a dynamic environment that the WiFi Pineapple artfully navigates for optimal traffic interception.
- SSID (Service Set Identifier): The human-readable network name, or SSID, becomes a strategic tool for the WiFi Pineapple to emulate legitimate access points with finesse.
Tactical Traffic Interception: A Ballet of Techniques in Wireless Network Pentesting
1. Passive Packet Sniffing:
The WiFi Pineapple engages in a ballet of passive packet sniffing, where it gracefully listens to the airwaves, capturing data frames in a silent dance. This observant stance allows the device to intercept unencrypted traffic, providing a panoramic view of communication patterns essential for wireless network pentesting.
# Sniffing Wi-Fi traffic on a specific channel
airodump-ng -c [channel_number] --bssid [target_BSSID] -w capture_file wlan0monIn Wireshark, the captured frames can be analyzed. Management frames like association and reassociation requests reveal devices attempting to connect.
2. Probe Request Capture:
A strategic pas de deux in the WiFi Pineapple’s repertoire involves capturing probe requests from devices actively seeking Wi-Fi connections. As devices pirouette in search of a network, the WiFi Pineapple gracefully seizes this moment to identify devices in its wireless ballet.
# Capturing probe requests on a specific channel
airodump-ng -c [channel_number] --bssid [target_BSSID] --output-format pcap -w probe_capture wlan0monWireshark analysis of the probe request frames provides insights into devices actively seeking network connections.
3. Dynamic Channel Hopping:
The WiFi Pineapple executes a dynamic channel hopping routine, gracefully navigating between Wi-Fi channels. This dynamic dance ensures comprehensive coverage of the radio frequency spectrum, adapting elegantly to the ever-changing wireless landscape.
# Dynamic channel hopping with Airodump-ng
airodump-ng --band abg wlan0monIn Wireshark, real-time adaptability can be observed as the WiFi Pineapple hops between channels, capturing frames.
Real-Time Web Interface: Conducting the Symphony of Wireless Network Pentesting
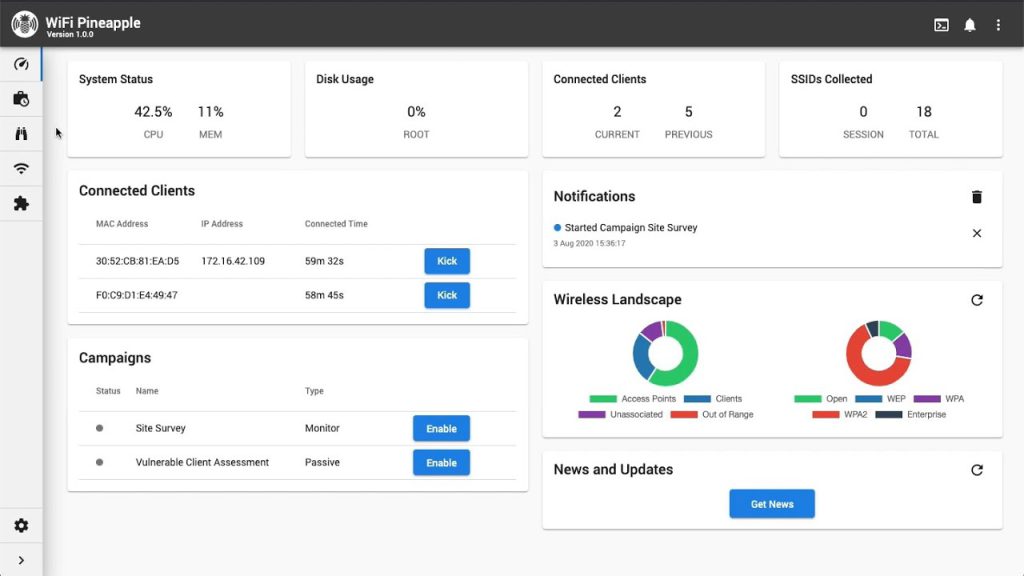
While the WiFi Pineapple engages in tactical traffic interception using the 802.11 protocol, its real-time web interface serves as the conductor’s baton for security professionals. This interface orchestrates dynamic adjustments, deploys payloads, and provides responsive control over the device’s operations in the grand symphony of wireless network pentesting.
# Deploying a payload via WiFi Pineapple web interface
curl -X POST -d 'payload=evil_script.sh' http://wifi-pineapple-ip:1471/api/payloadSecurity professionals can deploy payload modules through the web interface, orchestrating a cadence of automated tasks for a targeted testing approach.
Ethical Use and Responsible Testing: Navigating the Wireless Waltz with Integrity
While the WiFi Pineapple waltzes through the wireless landscape, ethical considerations remain at its core. Responsible testing practices ensure that security professionals navigate the airwaves with integrity, adhering to ethical standards and legal compliance in the realm of wireless network pentesting.
Guiding Ethical Principles:
- Explicit Authorization Encore: Secure explicit permission from network owners or administrators before deploying the WiFi Pineapple.
- Informed Consent Crescendo: Clearly communicate the scope and purpose of testing to prevent misunderstandings and ensure informed consent.
- Limited Public Use Finale: Avoid deploying the WiFi Pineapple in public spaces without explicit authorization to prevent unintended consequences during the grand finale of wireless network pentesting.
Hak5’s Wireless Symphony: Elevating Pentesting Artistry
For those eager to join the wireless network pentesting ballet, Hak5 provides an array of cutting-edge tools that elevate your security prowess. Step into the world of Hak5 and experience a symphony of wireless testing artistry by exploring their curated selection of tools here. Immerse yourself in the wireless landscape, guided by Hak5’s expertise, and refine your skills in the artful dance of wireless network pentesting.
Conclusion: A Grand Finale of Precision in Wireless Network Pentesting
In the grand theater of wireless network pentesting, the Hak5 WiFi Pineapple emerges not just as a tool but as a maestro orchestrating a grand finale with the 802.11 protocol. Its strategic use of passive sniffing, probe request capture, and dynamic channel hopping, coupled with real-time user interaction through the web interface, creates an environment where security professionals can navigate the wireless landscape with unparalleled finesse. As the WiFi Pineapple decodes the language of the airwaves, ethical use remains at its core, ensuring that the intricacies of wireless network pentesting are navigated with a symphony of integrity and responsibility.
This comprehensive exploration serves as a guide to the wireless ballet, inviting security professionals to not just understand but to master the artistry of the https://hak5.org WiFi Pineapple in wireless network pentesting. With each graceful move and strategic interception, the WiFi Pineapple contributes to the symphony of security, empowering ethical hackers to fortify networks and dance on the edge of innovation.
Leave a Reply